Microsoft Issues IE Security Advisory in Response to Attack Reports
Updated: 2012-12-31 18:15:00
 :
: Like many others, I’ve been in a number of debates about gun control in recent weeks. Here are my main thoughts on the topic:
The goal of any gun rights or legislation that limits those rights should be that of reducing suffering and increasing happiness for Americans. That is the moral goal, and all other considerations should be subordinate to it.
The Second Amendment held to that standard when it was created by attempting to ensure that America would be able to defend itself if attacked. Regardless of what we believe now to be the case, we must realize this was true at the time, could still be true now, and we must apply an EXTREMELY high standard to anything wishing to oppose that precedent.
Many are dying each year due to gun violence, and something should be done about that.
Emotional reactions to stimuli, especially when the solution requires a cool evaluation of data and the careful application of reason, is nearly always a poor idea.
Proof of emotion being a poor impetus for legislation is evident in recent “Assault Rifle” bans that focus on weapons that look “military” or hold magazines with too many rounds in them. These “feel” effective but absolutely are not. Looks don’t equate to function, and the recent mass shootings all employed multiple magazines–not a couple of them with large capacity.
Rather than focus on outlawing guns we should first do a comprehensive analysis of all mass shootings in the last 25 years and determine their attributes. What weapons? What was the legal status of the shooter? What was his mental status? Were the guns legal? What type were they? What types of magazines and ammunition were used? That data should be juxtaposed with any proposed legislation to determine if it would actually make a difference or if it merely “feels” effective.
Very few people think all guns should be illegal for law-abiding home owners, i.e. most think people should be allowed to own handguns and rifles on their own property, not only just as a natural right but also due to the second amendment.
Very few people think all guns should be legal–even for law-abiding home owners, e.g. rocket launchers and chemical weapons.
Since we agree on the extremes, the question is mostly one of where to mark the sand regarding what is allowed and not allowed, for who, and where.
I believe the best approach is not to ban guns for law-abiding citizens, but to instead implement very strict responsibility laws for anyone buying or selling them, and to conduct a massive program to remove unregistered weapons. Basically, ensure every gun out there is registered to someone with training for that type of weapon, and that they are aware they are responsible for anything that happens with the weapon. Suicide, accidental shooting, mass shooting massacre–they all fall on the head of the gun owner for not properly securing it. So, extremely high standards for gun ownership, with most all guns being obtainable, and extreme consequences for the gun owner if they are misused.
So, a course of action toward improvement might look like:
Take no emotional action after an incident. Any law passed during that time is likely to be significantly flawed.
Perform rigorous analysis of the attributes of the negative incidents of the last 25 years.
Measure all proposed legislation against the standard of helping in most, if not all, of those cases.
Raise the standards for attaining guns in the first place and confiscate all weapons that are not properly owned. This will include much more lengthy background checks, with strong focus on mental health.
Ensure that mental health situations are linked with gun possession, e.g. if someone is mentally ill in a family that has guns present, or the gun owner himself is mentally ill, action should be taken to ensure they do not become a threat.
Raise the punishments associated with someone’s gun being used improperly–even if they weren’t the ones using it.
Allow properly trained and law-abiding citizens to have most any type of gun, as the fact that it’s associated with them and they had to get certified on it will prevent most crime from anyone who would take those steps.
Remove the guns that are not properly owned in the fashion laid out above, and severely punish those who break laws related to their ownership and distribution.
In short, allow most any weapon to be obtained by law-abiding citizens who have gone through the proper, rigorous background checks and training commensurate with the type of weapon being requested. For concealed carry and other location-based laws, have additional training classes required, and open up reciprocity to be national rather than regional.For example, the standard for having a basic handgun or rifle in the home only would be fairly low. Proof of training on the weapon (safety and use), proof of legal purchase of the weapon, and proof of proper secure storage mechanism.
Then, when the owner wanted to add concealed personal carry, or carrying in their vehicle, to their permit, they would go through that training and certification as well. This would be extremely high quality training and it would be available to ANYONE who passes the background check that includes mental health, criminal record, etc. And the cost would be relatively negligible. The cost for the first level (weapons in home) would be virtually nothing so that you don’t have a fee to be compliant with the spirit of the 2nd amendment.
And if someone wanted a Berrett .50 sniper rifle, they could get that too. They prove they went to the course to use it, that they can safely store it, and that they don’t have any background issues that should prevent ownership of it, then the law gives them the benefit of the doubt. Of course, as the weapons get more extreme the scrutiny should as well. If you live 5 miles from a known militia group who has threatened the POTUS, then that’s perhaps a reason to deny the application. But these should be extremely rare.
There would also be regular retraining/recertification required according to the types of weapons owned, with most being very cheap all the way up through basic home weapons and basic weapons being concealed carry and carry in the car. The more exotic weapons could be more expensive to own just because of the training required and the additional risk (the money and training requirements are a good filter).
I think this type of system would both allow Americans to have their guns while simultaneously increasing the safety of the populace over what we have today. Gang violence with guns would largely go away because the guns wouldn’t be available, people with mental illness wouldn’t be committing so many mass shootings because gun owners would have strict control over legal weapons, and random acts of violence would be significantly more likely to be met with the weapons of law-abiding citizens who could stop the incident before it became worse.
Thoughts?
Related Posts:A Logical Approach To Gun LawsRight-To-Carry Laws Are GoodA Look at Obama’s View on Gun ControlGuns on University Campuses as a Microcosm of Larger SocietySome Thoughts on the Events in Newtown
Like many others, I’ve been in a number of debates about gun control in recent weeks. Here are my main thoughts on the topic:
The goal of any gun rights or legislation that limits those rights should be that of reducing suffering and increasing happiness for Americans. That is the moral goal, and all other considerations should be subordinate to it.
The Second Amendment held to that standard when it was created by attempting to ensure that America would be able to defend itself if attacked. Regardless of what we believe now to be the case, we must realize this was true at the time, could still be true now, and we must apply an EXTREMELY high standard to anything wishing to oppose that precedent.
Many are dying each year due to gun violence, and something should be done about that.
Emotional reactions to stimuli, especially when the solution requires a cool evaluation of data and the careful application of reason, is nearly always a poor idea.
Proof of emotion being a poor impetus for legislation is evident in recent “Assault Rifle” bans that focus on weapons that look “military” or hold magazines with too many rounds in them. These “feel” effective but absolutely are not. Looks don’t equate to function, and the recent mass shootings all employed multiple magazines–not a couple of them with large capacity.
Rather than focus on outlawing guns we should first do a comprehensive analysis of all mass shootings in the last 25 years and determine their attributes. What weapons? What was the legal status of the shooter? What was his mental status? Were the guns legal? What type were they? What types of magazines and ammunition were used? That data should be juxtaposed with any proposed legislation to determine if it would actually make a difference or if it merely “feels” effective.
Very few people think all guns should be illegal for law-abiding home owners, i.e. most think people should be allowed to own handguns and rifles on their own property, not only just as a natural right but also due to the second amendment.
Very few people think all guns should be legal–even for law-abiding home owners, e.g. rocket launchers and chemical weapons.
Since we agree on the extremes, the question is mostly one of where to mark the sand regarding what is allowed and not allowed, for who, and where.
I believe the best approach is not to ban guns for law-abiding citizens, but to instead implement very strict responsibility laws for anyone buying or selling them, and to conduct a massive program to remove unregistered weapons. Basically, ensure every gun out there is registered to someone with training for that type of weapon, and that they are aware they are responsible for anything that happens with the weapon. Suicide, accidental shooting, mass shooting massacre–they all fall on the head of the gun owner for not properly securing it. So, extremely high standards for gun ownership, with most all guns being obtainable, and extreme consequences for the gun owner if they are misused.
So, a course of action toward improvement might look like:
Take no emotional action after an incident. Any law passed during that time is likely to be significantly flawed.
Perform rigorous analysis of the attributes of the negative incidents of the last 25 years.
Measure all proposed legislation against the standard of helping in most, if not all, of those cases.
Raise the standards for attaining guns in the first place and confiscate all weapons that are not properly owned. This will include much more lengthy background checks, with strong focus on mental health.
Ensure that mental health situations are linked with gun possession, e.g. if someone is mentally ill in a family that has guns present, or the gun owner himself is mentally ill, action should be taken to ensure they do not become a threat.
Raise the punishments associated with someone’s gun being used improperly–even if they weren’t the ones using it.
Allow properly trained and law-abiding citizens to have most any type of gun, as the fact that it’s associated with them and they had to get certified on it will prevent most crime from anyone who would take those steps.
Remove the guns that are not properly owned in the fashion laid out above, and severely punish those who break laws related to their ownership and distribution.
In short, allow most any weapon to be obtained by law-abiding citizens who have gone through the proper, rigorous background checks and training commensurate with the type of weapon being requested. For concealed carry and other location-based laws, have additional training classes required, and open up reciprocity to be national rather than regional.For example, the standard for having a basic handgun or rifle in the home only would be fairly low. Proof of training on the weapon (safety and use), proof of legal purchase of the weapon, and proof of proper secure storage mechanism.
Then, when the owner wanted to add concealed personal carry, or carrying in their vehicle, to their permit, they would go through that training and certification as well. This would be extremely high quality training and it would be available to ANYONE who passes the background check that includes mental health, criminal record, etc. And the cost would be relatively negligible. The cost for the first level (weapons in home) would be virtually nothing so that you don’t have a fee to be compliant with the spirit of the 2nd amendment.
And if someone wanted a Berrett .50 sniper rifle, they could get that too. They prove they went to the course to use it, that they can safely store it, and that they don’t have any background issues that should prevent ownership of it, then the law gives them the benefit of the doubt. Of course, as the weapons get more extreme the scrutiny should as well. If you live 5 miles from a known militia group who has threatened the POTUS, then that’s perhaps a reason to deny the application. But these should be extremely rare.
There would also be regular retraining/recertification required according to the types of weapons owned, with most being very cheap all the way up through basic home weapons and basic weapons being concealed carry and carry in the car. The more exotic weapons could be more expensive to own just because of the training required and the additional risk (the money and training requirements are a good filter).
I think this type of system would both allow Americans to have their guns while simultaneously increasing the safety of the populace over what we have today. Gang violence with guns would largely go away because the guns wouldn’t be available, people with mental illness wouldn’t be committing so many mass shootings because gun owners would have strict control over legal weapons, and random acts of violence would be significantly more likely to be met with the weapons of law-abiding citizens who could stop the incident before it became worse.
Thoughts?
Related Posts:A Logical Approach To Gun LawsRight-To-Carry Laws Are GoodA Look at Obama’s View on Gun ControlGuns on University Campuses as a Microcosm of Larger SocietySome Thoughts on the Events in Newtown Instagram version.
Related Posts:Mount Diablo and the Moon<liOur Earth’s Timeline, Scaled to One YearHow the States Voted by EducationNew Cisco Switch For the HouseMe, According to Google
Instagram version.
Related Posts:Mount Diablo and the Moon<liOur Earth’s Timeline, Scaled to One YearHow the States Voted by EducationNew Cisco Switch For the HouseMe, According to Google Taken a few minutes ago on the 101.
Related Posts:Mount Diablo and the Moon IIOur Earth’s Timeline, Scaled to One YearHow the States Voted by EducationNew Cisco Switch For the HouseMe, According to Google
Taken a few minutes ago on the 101.
Related Posts:Mount Diablo and the Moon IIOur Earth’s Timeline, Scaled to One YearHow the States Voted by EducationNew Cisco Switch For the HouseMe, According to Google With news coming from Iran’s CERT of a nasty (but not really nasty) new piece of malware designed to wipe drives and desktop contents on a specific date, we took the straightforward approach of examining what common, easily implemented security best practices could have stopped Batchwiper in its tracks… As far as malware goes, Batchwiper [...]
With news coming from Iran’s CERT of a nasty (but not really nasty) new piece of malware designed to wipe drives and desktop contents on a specific date, we took the straightforward approach of examining what common, easily implemented security best practices could have stopped Batchwiper in its tracks… As far as malware goes, Batchwiper [...]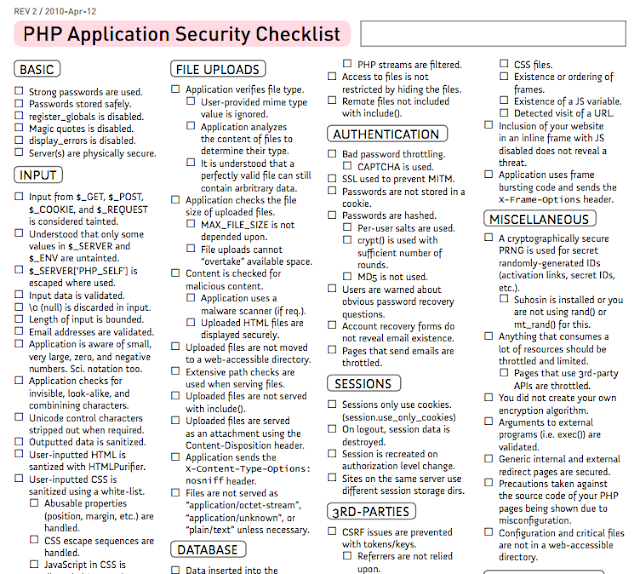
 : Internet Network Security Blog How to Speak Data Center : IT Power Supplies December 14, 2012 at 1:12 pm Filed under Uncategorized In my first two posts on how IT pros can improve their interactions with data center facility pros , I covered the difference between power and energy and how to covert between kWh and BTUs This post will address power supply ratings and power supply . efficiency IT and data center professionals need to understand how much power IT equipment uses . You may have heard of a quick-and-dirty option to use the nameplate” power rating to estimate energy use . The nameplate is a safety label that comes from the Underwriters Laboratory which was formed in the year 1894 for the independent evaluation of electrical products for . safety Despite the nameplate’s function
: Internet Network Security Blog How to Speak Data Center : IT Power Supplies December 14, 2012 at 1:12 pm Filed under Uncategorized In my first two posts on how IT pros can improve their interactions with data center facility pros , I covered the difference between power and energy and how to covert between kWh and BTUs This post will address power supply ratings and power supply . efficiency IT and data center professionals need to understand how much power IT equipment uses . You may have heard of a quick-and-dirty option to use the nameplate” power rating to estimate energy use . The nameplate is a safety label that comes from the Underwriters Laboratory which was formed in the year 1894 for the independent evaluation of electrical products for . safety Despite the nameplate’s function In a recent post from Xconomy, Gregory T. Huang sat down with Veracode CEO Bob Brennan for a quick interview. The two talked about industry tipping points, how Veracode technology and strategy differs from our competitors and Bob's unique insight on leadership and company culture.
In a recent post from Xconomy, Gregory T. Huang sat down with Veracode CEO Bob Brennan for a quick interview. The two talked about industry tipping points, how Veracode technology and strategy differs from our competitors and Bob's unique insight on leadership and company culture. : Internet Network Security Blog Network Overlays : An Introduction December 11, 2012 at 4:33 pm Filed under Uncategorized While network overlays are not a new concept , they have come back into the limelight thanks to drivers brought on by large-scale virtualization . Several standards have been proposed to enable virtual networks to be layered over a physical network infrastructure : VXLAN , NVGRE , and SST . While each proposed standard uses different encapsulation techniques to solve current network limitations , they share some similarities . Let’s look at how network overlays work in . general Many advanced virtualization features require Layer 2 adjacency , which is the ability to exist in the same Ethernet broadcast domain . This requirement can cause broadcast domains to grow to
: Internet Network Security Blog Network Overlays : An Introduction December 11, 2012 at 4:33 pm Filed under Uncategorized While network overlays are not a new concept , they have come back into the limelight thanks to drivers brought on by large-scale virtualization . Several standards have been proposed to enable virtual networks to be layered over a physical network infrastructure : VXLAN , NVGRE , and SST . While each proposed standard uses different encapsulation techniques to solve current network limitations , they share some similarities . Let’s look at how network overlays work in . general Many advanced virtualization features require Layer 2 adjacency , which is the ability to exist in the same Ethernet broadcast domain . This requirement can cause broadcast domains to grow to One of the things we clearly see in our platform is that more vendor applications are being tested. Our SoSS reports are not based on surveys that collect opinions, it is an analysis of data aggregated from companies as they test and secure their applications. Our platform tracks whether an application is being tested as part of an enterprise effort to test vendor software. The number of vendor apps tested is rising every quarter.
One of the things we clearly see in our platform is that more vendor applications are being tested. Our SoSS reports are not based on surveys that collect opinions, it is an analysis of data aggregated from companies as they test and secure their applications. Our platform tracks whether an application is being tested as part of an enterprise effort to test vendor software. The number of vendor apps tested is rising every quarter.